In this post, I am releasing a PowerShell POC script that will scan the specified target hosts and attempt to detect those that are vulnerable to VMware vCenter CVE-2021-21972.
You can find the script, Invoke-CVE-2021-21972-Scan.ps1, on my github here:
https://github.com/robwillisinfo/VMware_vCenter_CVE-2021-21972
The script executes in the following order:
- Create a log file, default log name is Invoke-CVE-2021-21972-Scan-output.txt
- Scan each target host by performing the following:
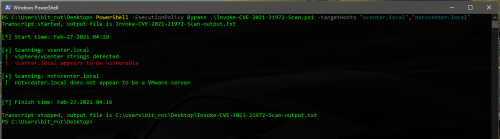
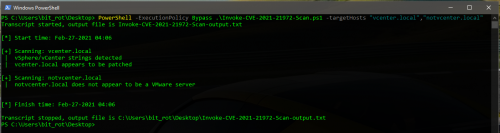
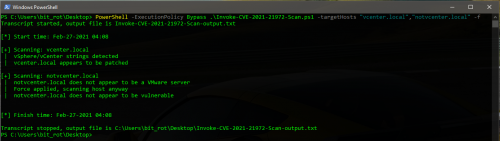
- Check the root domain for vSphere/vCenter strings
- If not found, check the /ui/ (HTML5 UI) directory for vSphere/vCenter strings
- If not found, no vulnerability scan is performed unless -f/-force parameter is specified
- If strings are found, make a GET request to /ui/vropspluginui/rest/services/uploadova looking for the following responses:
- 405 – Server is likely vulnerable
- 401 – Server is likely patched
- Other – Server is not vulnerable
Examples
Basic usage:
C:\PS> PowerShell.exe -ExecutionPolicy Bypass .\Invoke-CVE-2021-21972-Scan.ps1 -targetHosts “vcenter.local”,”vcenter.net”
All options with force scan:
C:\PS> PowerShell.exe -ExecutionPolicy Bypass .\Invoke-CVE-2021-21972-Scan.ps1 -targetHosts “vcenter.local”,”vcenter.net” -outputFile “output.txt” -force
All options with force scan (shorthand version):
C:\PS> PowerShell.exe -ExecutionPolicy Bypass .\Invoke-CVE-2021-21972-Scan.ps1 -t “vcenter.local”,”vcenter.net” -o “output.txt” -f