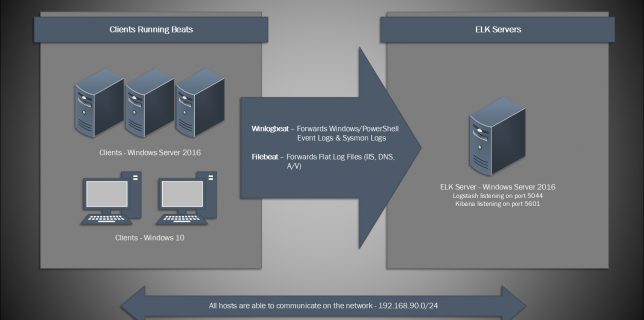
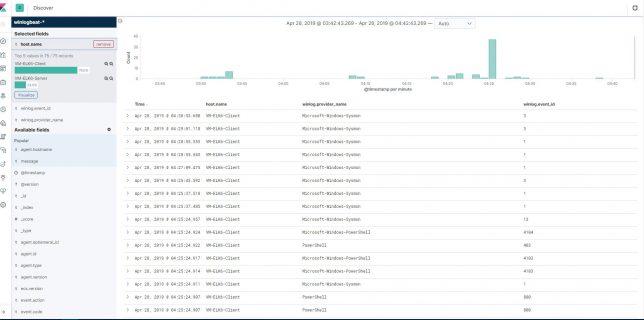
Gathering Windows, PowerShell and Sysmon Events with Winlogbeat – ELK 7 – Windows Server 2016 (Part II)
In part I of this series, Installing ELK 7 (Elasticsearch, Logstash and Kibana) on Windows Server 2016, I covered the following: Installing and configuring Elasticsearch, Logstash, and Kibana as Windows services Installing and configuring Winlogbeat to forward logs from the Continue reading