In the previous two posts I went over everything from installing Ubuntu to getting the ELK stack setup and ingesting logs from itself. Now in this final post in the series I am going to cover collecting Windows Event and IIS logs from remote Windows clients.
Here is the quick run down of exactly what is going to be covered in this post:
- Installing and configuring Winlogbeat
- Installing and configuring Filebeat
- Updating Kibana with the new index patterns
Testing Connectivity to the ELK Server
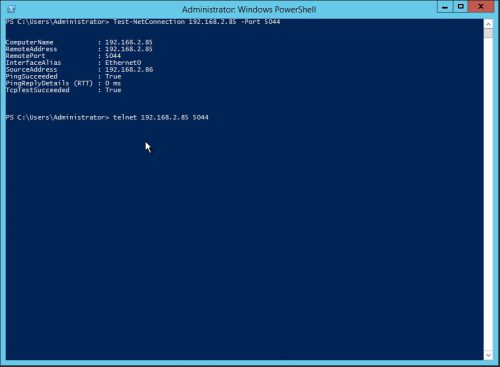
Before you begin shipping logs to the ELK stack from a remote machine it is generally a good idea to test network connectivity between the two machines. To do this from a Windows machine you can use one of the following commands to test port 5044 (Beats listener).
Powershell:
PS C:\> Test-NetConnection <IPAddressofELKServer> -Port 5044
Telnet:
PS C:\> telnet <IPAddressofELKServer> 5044
Installing WinLogbeat for Windows Logs
1.) Download Winlogbeat from https://www.elastic.co/downloads/beats
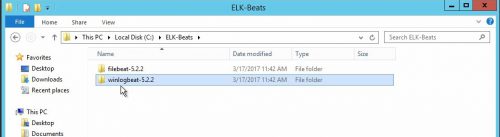
2.) Extract the zip archive to where you would like to run the agent from, in this example I will use C:\ELK-Beats.
3.) Once complete, CD to the path where the packages were extracted and run the install-service-winlogbeat.ps1 Powershell script found in the directory using the following command:
PS C:\> cd c:\ELK-Beats\winlogbeat-5.2.2
PS C:\ELK-Beats\winlogbeat-5.2.2> PowerShell.exe -ExecutionPolicy Bypass -File install-service-winlogbeat.ps1
4.) Next open the winlogbeat.yml configuration file found in the Winlogbeat directory and then edit the following lines:
# Comment out #output.elasticsearch: # Array of hosts to connect to. #hosts: ["localhost:9200"] # Uncomment and set Logstash IP output.logstash: # The Logstash hosts hosts: ["192.168.2.85:5044"]
Make sure to swap out the 192.168.2.85 with the IP address of the ELK stack server.
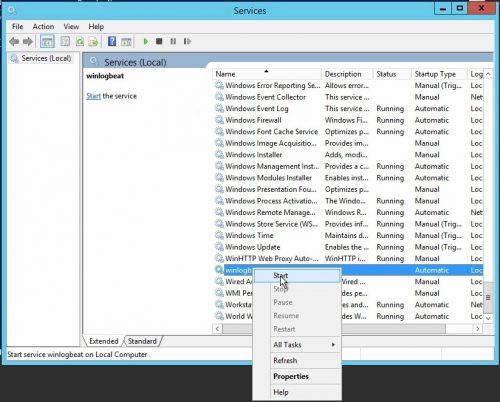
5.) Open services.msc, restart the Winlogbeat service and verify it is now running.
Installing Filebeat for IIS Logs
1.) Download Filebeat from https://www.elastic.co/downloads/beats
2.) Extract it to where you would like to run the agent from, I am going to use the same base path I used for Winlogbeat – C:\ELK-Beats.
3.) Once complete, CD to the path where the packages were extracted and run the install-service-filebeat.ps1 Powershell script found in the directory using the following command:
PS C:\> cd c:\ELK-Beats\filebeat-5.2.2
PS C:\ELK-Beats\filebeat-5.2.2> PowerShell.exe -ExecutionPolicy Bypass -File install-service-filebeat.ps1
4.) Next open the filebeat.yml configuration file found in the Filebeat directory and then edit the following lines:
# Add the path to IIS Logs
paths:
- C:\inetpub\logs\LogFiles\*\*
# Comment out
#output.elasticsearch:
# Array of hosts to connect to.
#hosts: ["localhost:9200"]
# Uncomment and set Logstash IP
output.logstash:
# The Logstash hosts
hosts: ["192.168.2.85:5044"]
5.) Open services.msc, restart the Filebeat service and verify it is now running.
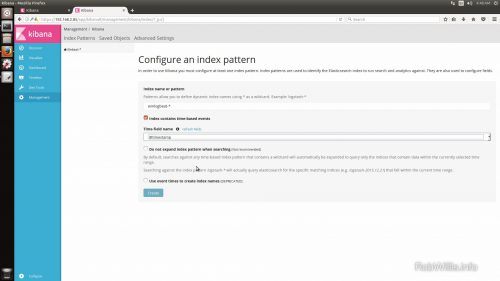
Add and update the index patterns in Kibana
1.) In Kibana under Management > Index Patterns, add the pattern for winlogbeat-*.
Wrap up
And that concludes this series, you should now have everything need to get the ELK stack services up and running on Ubuntu. You should also have a decent idea of how to start collecting logs from both Windows and Linux machines.