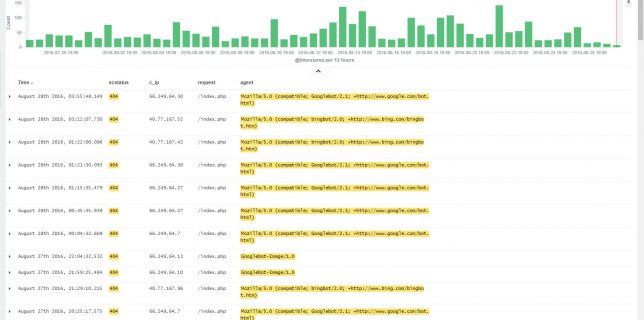
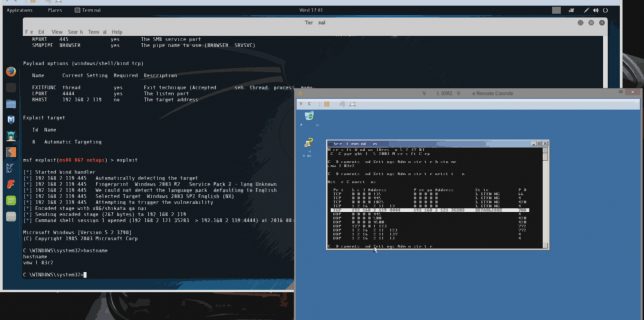
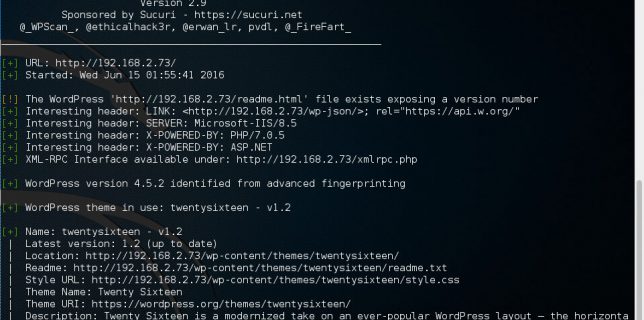
ELK 5 on Ubuntu 16.04
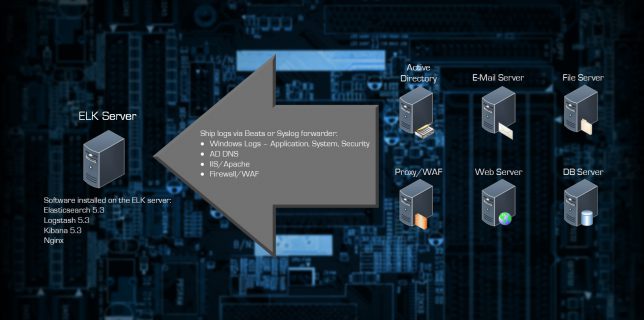
In this series of posts I am going to cover everything needed to get Elasticsearch, Logstash and Kibana (ELK) up and running on Ubuntu 16.04. In the videos I use the desktop version of Ubuntu, but the process should be Continue reading